
[ad_1] I often hear companies say they need to act faster — ideally in real time — with limited resources. They tell me they are excited...


[ad_1] Enacted in December, the European Union’s Cyber Resilience Act (CRA) introduces a set of mandatory security requirements for all commercial products with digital elements. The...

[ad_1] Retrieval-augmented generation (RAG) has emerged as a leading method for combating hallucinations and other inaccuracies that affect large language model (LLM) content generation. However, the...


[ad_1] Google today published a new paper that aims to quantify the environmental impact of its Gemini models. The researchers found that the “median Gemini Apps...


[ad_1] WebAssembly (Wasm) debugging remains, understandably, a challenge for this relatively new and exciting technology that is still evolving. Originally designed for the browser, it functions...

[ad_1] As engineering leaders race to build agentic AI solutions, many plan big infrastructure buys. Most do not need them. The fully open source data platforms...
[ad_1] Kubernetes is the cornerstone of cloud native architecture, but this container orchestrator is not the only thing that keeps enterprise stacks standing tall. From the...
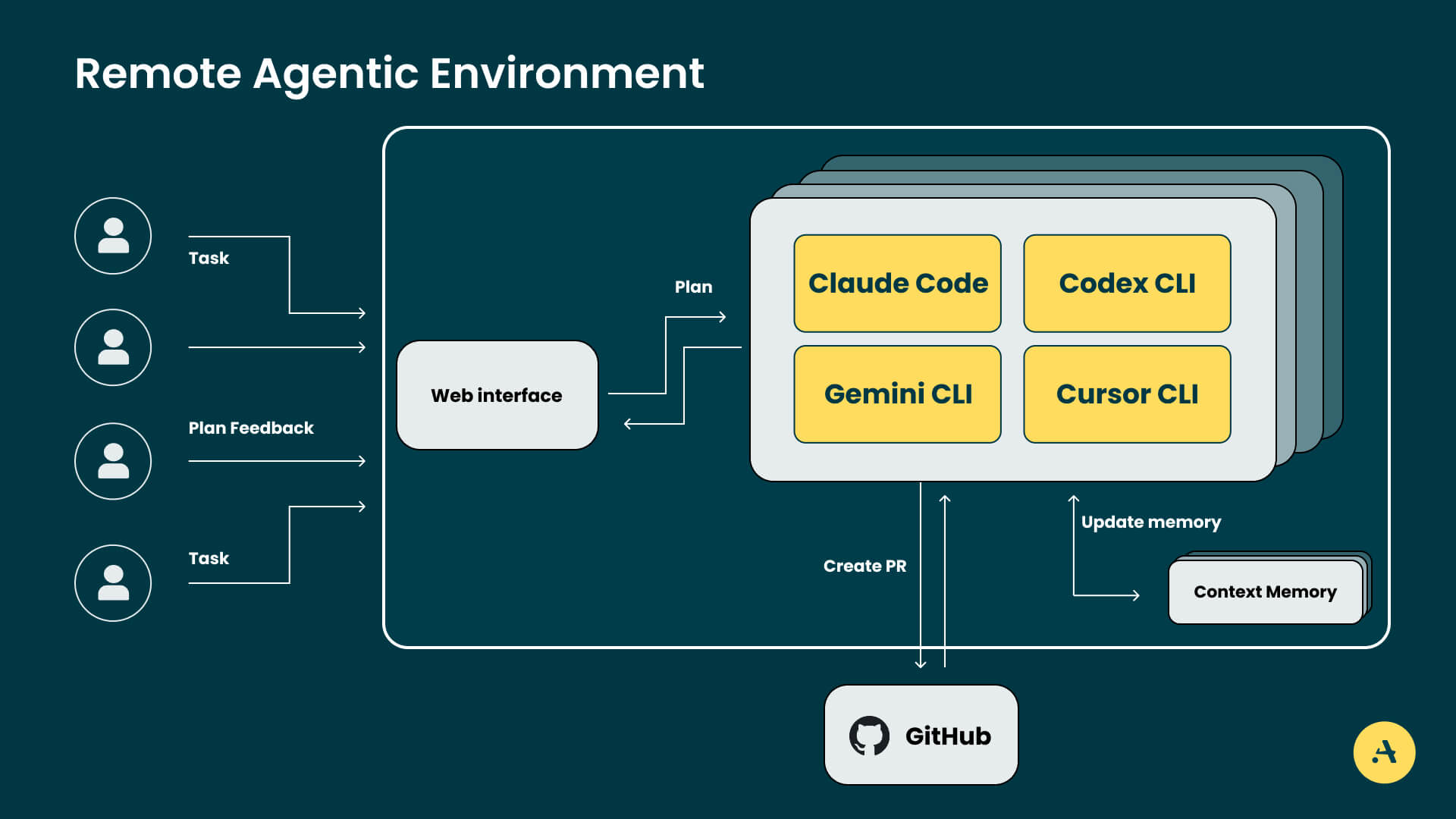
[ad_1] Imagine a scenario where a team of developers assigns this task to an AI system: “Migrate our user authentication from JWT tokens to OAuth 2.1...

[ad_1] MCP-UI is a new open source project that provides a way to add web-based user interface components to AI agents. It builds on the already...


[ad_1] Python developers have always faced a trade-off: write elegant, readable code or go for high performance. For a long time, this meant reaching for C...